VORACLE Attack: Are VPN Unlimited Users Safe?

Updated on July 13, 2021: From now on, traffic filtering, malware protection, and suspicious DNS activity blocking are available as a part of the separate DNS Firewall app.
Breaking news has set the world of VPN services on fire. On August 11, 2018, the 26th DEF CON Hacking Conference was hosted in Las Vegas, Nevada. Ahamed Nafeez, an independent speaker and security researcher, reported about a discovered vulnerability in the OpenVPN® protocol, called VORACLE attack. This is a loophole that potentially allows cybercriminals to reveal VPN users private data. VORACLE attack can affect VPN services that are based on OpenVPN® protocol.
Our team is sure you should stay on top of the cyber security news. That’s why we’d like to get things straight and tell you everything about this attack in detail. What is OpenVPN® protocol? How does the VORACLE attack work? Are VPN Unlimited users safe? Keep reading and get the answers!
What is OpenVPN® protocol?
First things first, let’s figure out what this protocol is and what its vulnerability appeared to be. VPN protocol is a set of processes that ensures that your VPN connection is fast and safe. In a nutshell, it is an algorithm suite that connects your device to a VPN server. VPN apps often offer their users a variety of protocols.
OpenVPN®, in turn, is the youngest and most widely used protocol. One of its main advantages is an open-source nature that allows developers to freely modify this protocol. It runs over User Datagram Protocol (UDP) or Transmission Control Protocol (TCP) tunnels, making users’ VPN traffic indistinguishable from a standard one. OpenVPN® also supports popular operating systems such as iOS, macOS, Windows, Android, and Linux.
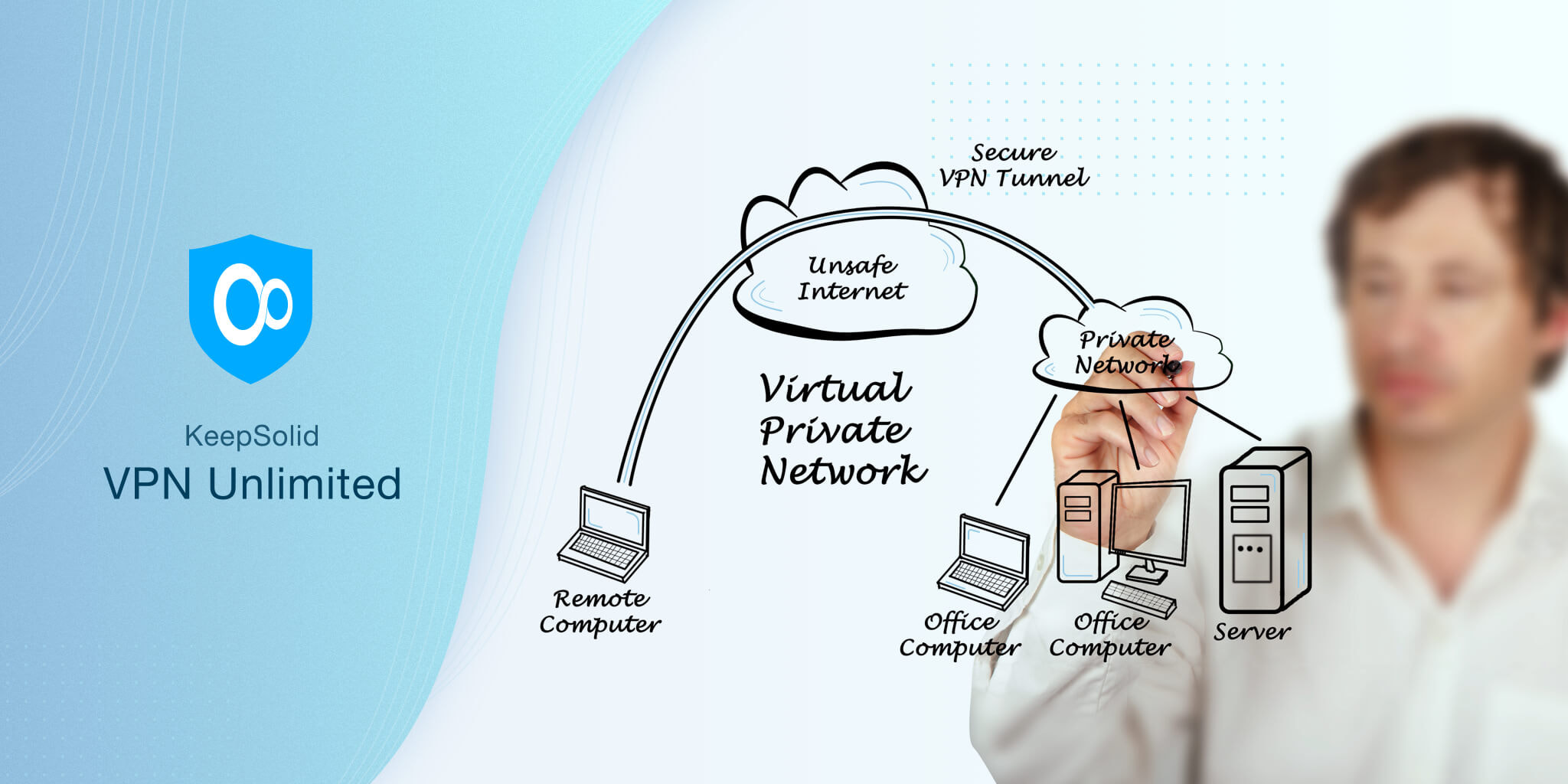
The weakness of OpenVPN® protocol turned out to be in its compression algorithms. The thing is, in order to encrypt your private data, OpenVPN® has to compress it first. This is made to expedite the work of a VPN app. Unfortunately, this played a trick on OpenVPN protocol users.
How does VORACLE attack work?
Long story short, VORACLE can decode HTTP traffic of VPN users. HTTP stands for Hypertext Transport Protocol and it is a basic insecure protocol of websites. You can identify such a website by http:// in its link address (learn more about how to recognize a suspicious link in our previous article). So, if a hacker lures a user to a compromised website, the VORACLE attack can reveal their personal data while OpenVPN® is compressing it.
In order for a hacker to successfully use VORACLE attack, certain conditions should be met:
- You use a VPN app that enables compression by OpenVPN® protocol
- Cyber criminal has to be in the same network as you are
- You use a web browser that is vulnerable to VORACLE attack (any web browser except Google Chrome)
- You visit a website with HTTP connection
- Hacker controls the aforementioned website or has previously inserted a malicious code to a legitimate site
Are VPN Unlimited users safe?
Absolutely! Since VPN Unlimited developers fixed this vulnerability in our OpenVPN® protocol, the users of our security solution are completely safe. The privacy of our users is our key concern and we did our best to ensure that you are secured. VORACLE attack caused a huge stir among VPN society. But in fact, its effectiveness is limited by the difficulty of its performance. Our team left no chance for cyber criminals to use it, so you have nothing to worry about.
“OpenVPN” is a registered trademark of OpenVPN Inc.