IKEv2 vs IKEv1 vs OpenVPN® (TLS) vs L2TP/IPsec vs PPTP – VPN Protocol Comparison

Updated on July 13, 2021: From now on, traffic filtering, malware protection, and suspicious DNS activity blocking are available as a part of the separate DNS Firewall app.
Rejoice, Windows users! VPN Unlimited finally grants you access to IKEv2 – the most secure, up-to-date, and reliable VPN protocol. What is IKEv2, exactly? How does it fare compared to other protocols? How to configure it? Read on and learn this and much more!
Best VPN protocols?
VPN protocol is a set of technologies used by VPN service providers to create a secured connection between a user and a website. It usually consists of at least two important parts – tunneling protocol that defines how devices within the network are connected, and encryption protocol that defines how the data traffic is secured.
Besides those two, different VPN protocols might offer additional features that are intended to provide users with new opportunities or to fix some known problems. Now, let’s take a look at the most popular virtual private network protocols and compare their pros and cons.
- PPTP
This one is the most “old-school” of them. The Point-to-Point Tunneling Protocol is technically not a VPN protocol, but is often utilized as such. It was developed in late 90’s and by default does not feature data encryption at all. It is still somewhat popular due to easy set-up and fast performance.
Most networks that use PPTP have to apply additional security measures or be deemed completely inappropriate for the modern internet environment. At the same time, doing so means negating the aforementioned benefits of the protocol to some point. So no matter how you slice it, using PPTP is a lose-lose scenario. - L2TP/IPsec

This protocol is just as easy to set up as PPTP and features reliable data security with AES-256 encryption. Alas, due to certain operational aspects (use of UDP port 500) it can be easily blocked. Also, the double encapsulation method of data protection makes L2TP/IPsec slower than PPTP and involves higher CPU usage. - OpenVPN®
Now, OpenVPN® is a full-fledged VPN protocol. It applies numerous security measures to ensure a great level of data protection. Among them is TLS (Transport Layer Security) – a widely deployed cryptographic protocol that ensures the privacy and reliability of the established connection.
In general, OpenVPN® utilizes various third-party software, which adds a number of handy features. It is open source, highly configurable, and is able to tackle all sorts of tasks. At the same time, this means that OpenVPN® requires technical knowledge to set up and configure. Also, its dependence on third-party solutions makes this protocol prone to occasional technical problems and suboptimal performance.
- IKEv1
Internet Key Exchange is a protocol based on IPsec, designed with privacy in mind. Its goal is to establish a secure authenticated communications channel and encrypt further communications. Among the benefits of the first version of this protocol are good performance speed and high-grade encryption support (though IKE is still not quite as secure as OpenVPN®).
Unfortunately, IKEv1 was prone to certain system problems, such as issues of compatibility between different IKE implementations, overall complicated structure, blocking by some firewalls, lack of mobile support, etc. This made it not too popular between users and service providers alike. - IKEv2
The second generation of IKE protocol was developed to fix most of the problems of its predecessor while keeping its benefits of high speed and good data security. Thus, IKEv2 features firewall traversal, Mobility support, simplified message exchange, and other handy improvements. Also, this protocol is highly reliable when switching between internet connections, like from WiFi to Ethernet.
Among the only cons that still exist in IKEv2 are complexity of implementation at the server-end and a bit weaker security compared to OpenVPN®. Still, it is currently one of the best VPN protocols out there, with more and more network-related companies turning their attention to it.
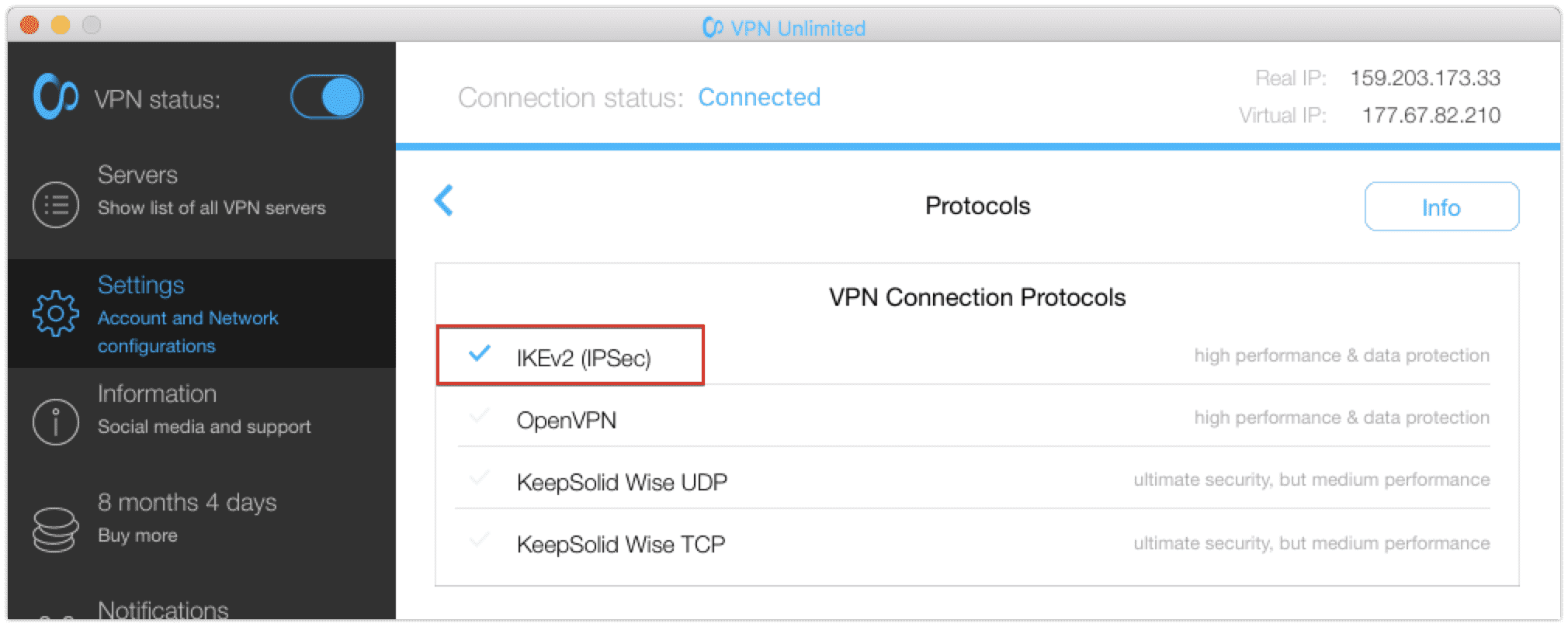
How to turn on IKEv2 on Windows, macOS, and iOS
VPN Unlimited’s Windows users can finally enjoy the advantages of IKEv2, as its support has recently been implemented in the Windows version of our app. You can choose this protocol from the Settings > Protocols menu of VPN Unlimited on Windows, macOS, and iOS. Try it out!
“OpenVPN” is a registered trademark of OpenVPN Inc.