Let’s Talk about Cybersecurity: TLS vs SSL, HTTPS, and Secure Browsing

Updated on July 13, 2021: From now on, traffic filtering, malware protection, and suspicious DNS activity blocking are available as a part of the separate DNS Firewall app.
SSL, TLS, SHA, RSA, CA… With all its numerous acronyms cybersecurity can be quite confusing! Let’s eliminate some blind spots together. In this piece, we’ll focus on the technologies that make your browsing secure. Read on and find out what is SSL/TLS security, how SSL/TLS works, how it is related to HTTPS, how it compares to VPN services like VPN Unlimited, and more.
- What is SSL and TLS?
- How SSL/TLS provides security to websites
- How SSL/TLS works
- Steps involved in the SSL/TLS handshake
- Are you absolutely secure using SSL/TLS connection
- HTTPS vs VPN: Do you need VPN if the website uses HTTPS
- Bottom line on SSL/TLS, HTTPS, and secure browsing
What is SSL and TLS?
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols that provide data authentication and encryption between servers, applications, and applications over a network. So, when a client (your device) connects to a web server, SSL and TLS ensure the security of communications between them.
SSL and TLS history
SSL, the predecessor of TLS, was originally developed by Netscape. The version 1.0 was never released due to serious security flaws. The first official version, SSL v.2.0, was issued in 1995, but because of a number of vulnerabilities still remained, just a year later it was replaced by SSL v3.0.
TLS, a stronger and more secure version of SSL based on SSL 3.0, was introduced in 1999. The majority of browsers and devices now use TLS v.1.2. However, to avoid confusion TLS is often called just SSL/TLS.
Both SSL 2.0 and 3.0 turned out not secure enough and were deprecated by the Internet Engineering Task Force (IETF) in 2011 and 2015 correspondingly.
How SSL/TLS provides security to websites

SSL/TLS is what adds up security to HTTP (Hypertext Transfer Protocol) making it HTTPS, where the final S letter stands for Secure. HTTP is an application-level protocol that transfers data between a browser and a web server. Simply put, it transfers your search results to your web browser.
HTTP connections aren’t safe as they don’t encrypt your data. Anyone intercepting your traffic can read it and steal your login, password, credit card details, and other sensitive information you entered.
For this reason HTTPS was created, the combination of HTTP handling data transfer and SSL/TLS carrying out data encryption. The SSL/TLS aspect makes your data much safer. If somebody snoops on HTTPS traffic, the data would look gibberish to them.
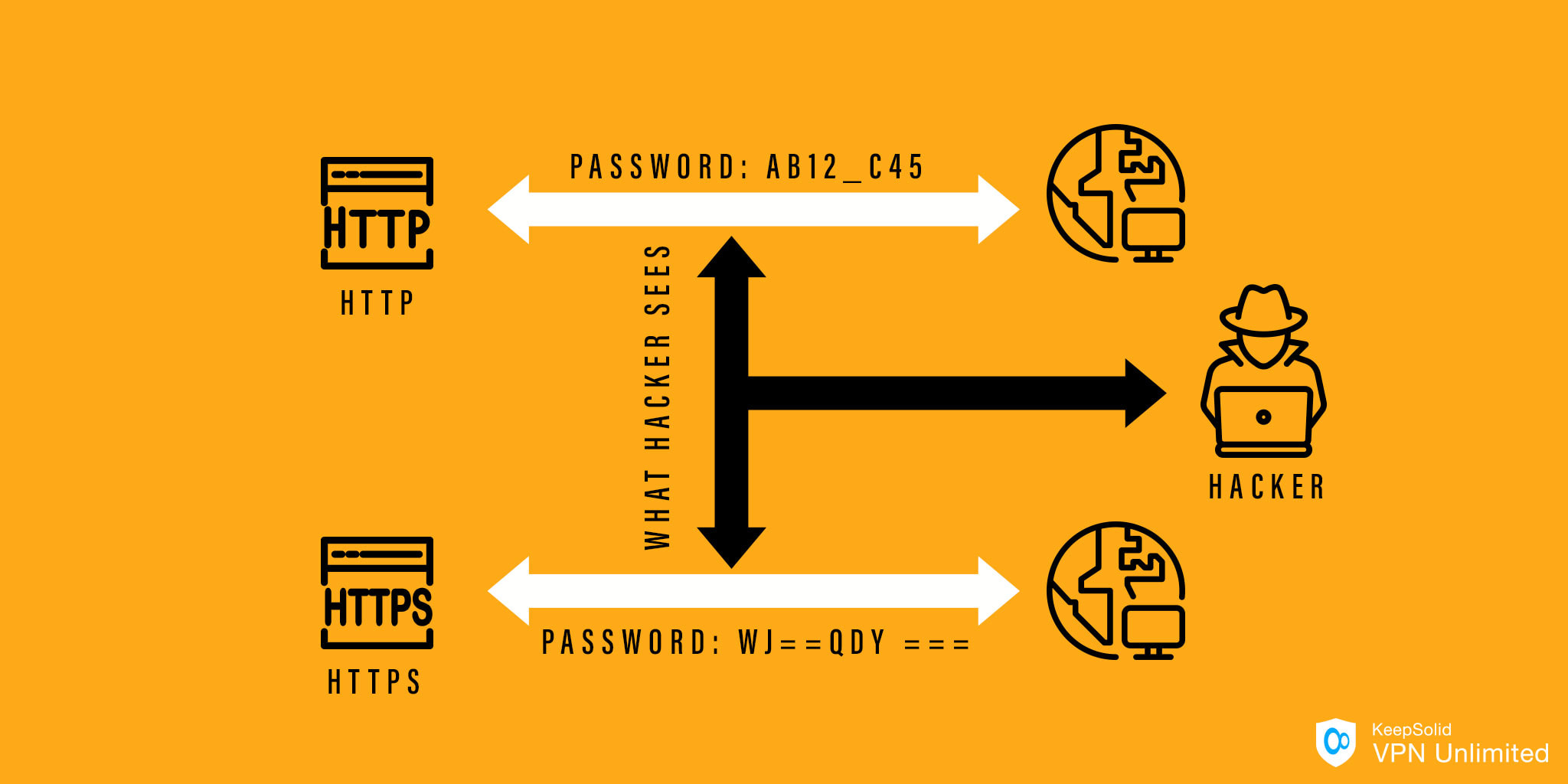
Nowadays, most websites use HTTPS. By the way, the URL bar is where you can check it.
How SSL/TLS works
To establish secure SSL/TLS connection, the browser and the server use SSL Certificate. It is a type of digital certificate required during the SSL/TLS handshake process to authenticate the identity of the website and enable the encrypted connection.
The SSL/TLS handshake is what the communication over SSL/TLS always begins with. There are two parties involved: the client and the server, coming across each other for the first time to secure their communication. For this, SSL/TLS protocols use a combination of asymmetric and symmetric encryption.
Asymmetric cryptography, also known as public-key cryptography, is the cryptographic system that uses a pair of 2 different keys (hence the name asymmetric) during the encryption and decryption processes.
One key in the pair can be shared with everyone and is thus called the public key. The other key is kept secret, so that only the intended recipient can decrypt the message. This key is called the private key.
A message encrypted with one’s public key can only be decrypted by their private key and the other way round.
Symmetric cryptography involves only one secret key used by both sides (hence the name it is symmetric) to encrypt and decrypt information. Though being less secure, symmetric encryption is much faster compared to the asymmetric technology.
The SSL/TLS handshake lets the browser verify the web server, get the public key, and set up a secure connection before starting the actual data transfer.
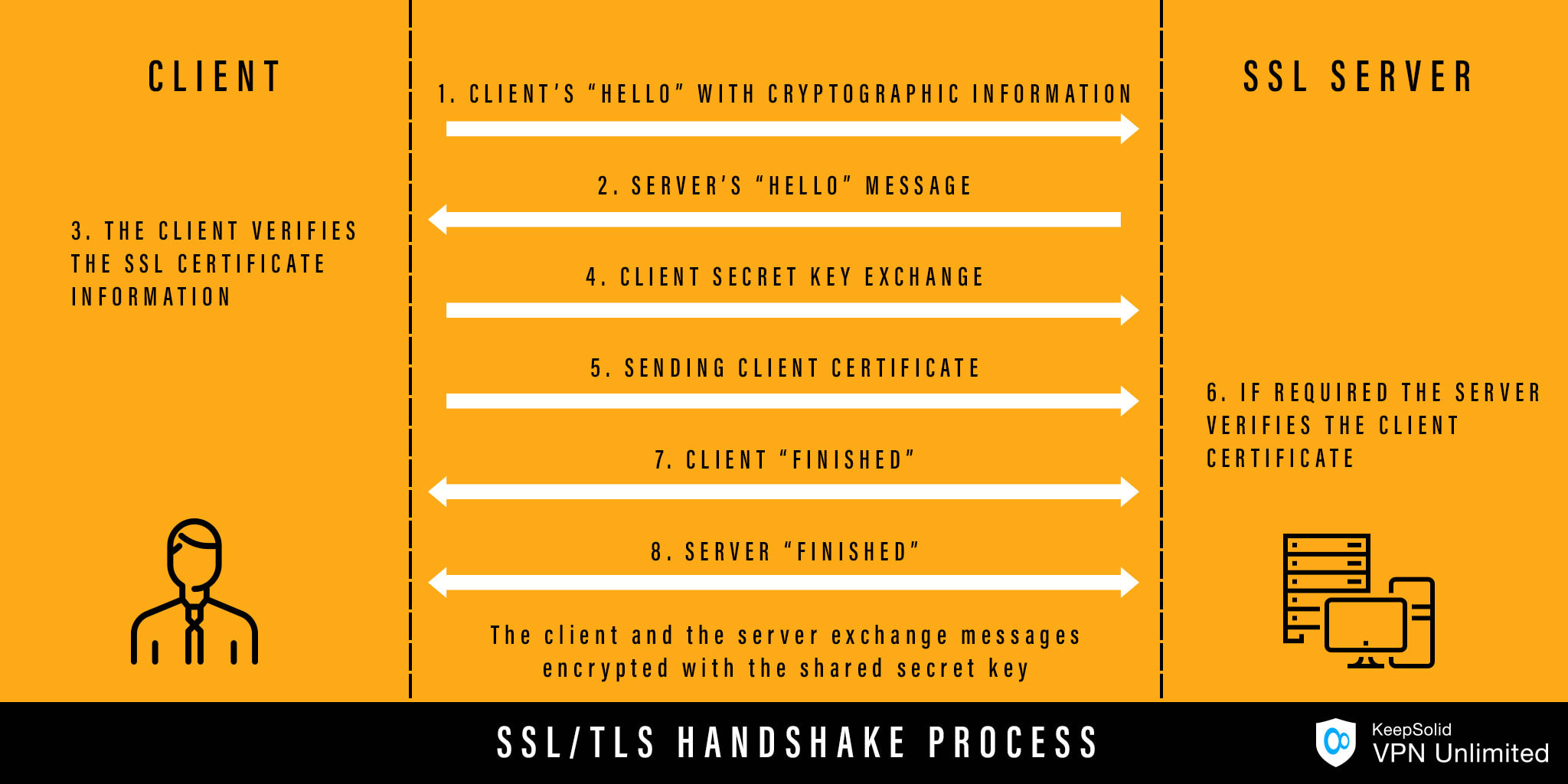
Steps involved in the SSL/TLS handshake
The SSL/TLS handshake starts from validation of the other party’s identity and concludes with the generation of a common key – a secret key. The detailed process of establishing a secure SSL/TLS connection includes the following steps:
- The SSL or TLS client sends a “hello” message to the web server it wants to communicate with. The message contains such cryptographic information as the SSL or TLS version and types of ciphers the client supports.
- The SSL or TLS server sends back the “hello” message with its public key and SSL certificate. The two communicating parties use the asymmetric cryptography for secure message exchange.
- The SSL or TLS client verifies the server’s certificate.
- The client then sends a random byte string that lets both the client and the server to compute the secret key. This secret key will be used for encrypting the subsequent message information. The random byte string itself is also encrypted, with the server’s public key.
- In case the server requested the client’s certificate, the latter sends an encrypted (with the client’s private key) random byte string, together with the client’s certificate.
- The SSL or TLS server verifies the client’s certificate.
- The client forwards the server a “finished” message, encrypted with the secret key. Sending the message indicates that the client’s part of the handshake is complete.
- The server completes its part of the handshake the same way – by sending the client a “finished” message, encrypted with the secret key.
After that, during the SSL or TLS session the server and client exchange messages now using only symmetric encryption and the shared secret key. You may wonder, why not use the more secure asymmetric encryption?
Asymmetric encryption is indeed more secure, that is why it was employed to generate a shared secret key. But after that, once the integrity of communication in ensured, you only need symmetric encryption, which makes the client – server communication much faster.
Are you absolutely secure using SSL/TLS connection?
The SSL/TLS certificate, when installed on a web server, allows secure connections between the server and a browser (remember the HTTPS protocol we mentioned before?). However, which protocol will be used during your connection, TLS or the outdated SSL, is defined not by the SSL/TLS certificate, but by your browser and the target server’s configurations.
This means that it’s possible to connect to a HTTPS website that uses an outdated SSL v3.0 protocol. Which is vulnerable to cyber attacks. Most web browsers will indicate that by crossing the padlock and HTTPS symbols in the URL, but who of us checks this panel?
HTTPS vs VPN: Do you need VPN if the website uses HTTPS

HTTPS and the VPN technology perform somewhat similar functions and some people may confuse the two. Both tools are used to protect your privacy, but to different extent.
A trusted VPN service like VPN Unlimited reliably encrypts both your browser’s and apps’ internet traffic. It hides your real IP address and location, letting you opt out of ISP surveillance and third party tracking. On top of it, VPN software opens up access to geo-blocked web content, so you can surf the web and even stream Hulu and other resources without any restrictions, wherever you are!
Go both secure and private online with VPN Unlimited!
HTTPS, on the other hand, encrypts only the information you enter on a website. It doesn’t hide your location or protect privacy, so your ISP and other parties will still be able to see what websites you visit. Also, HTTPS can’t help you overcome internet censorship.
If you seek for a safe, private, and unrestricted internet access, combining HTTPS and a VPN service is what you need.
Bottom line on SSL/TLS, HTTPS, and secure browsing
SSL and TLS cryptographic protocols make browsing more secure. Websites using HTTPS is what you should definitely pay attention to before entering your sensitive data like credit card details.
And if you want to boost your security, go anonymous and absolutely free online, make sure to enable VPN Unlimited!