Top 5 Threats to Your Online Privacy
Updated on July 13, 2021: From now on, traffic filtering, malware protection, and suspicious DNS activity blocking are available as a part of the separate DNS Firewall app.
Think your online activity, including fasting posts in social networks or geo-marks in visited places, won’t attract attention of anyone except your friends and family? Sure that strong passwords to your accounts will secure them from adversaries? This is a big mistake. When sharing personal information through the internet, you voluntarily give necessary hints to scammers, snoopers, and others in the cyberspace on how to access your account and use it in their deceptive purposes. Don’t forget that we live in the era of high technology, where the impossible becomes real.
Follow our post and learn more about main threats to your online privacy that are always on the lookout while you are surfing the web.
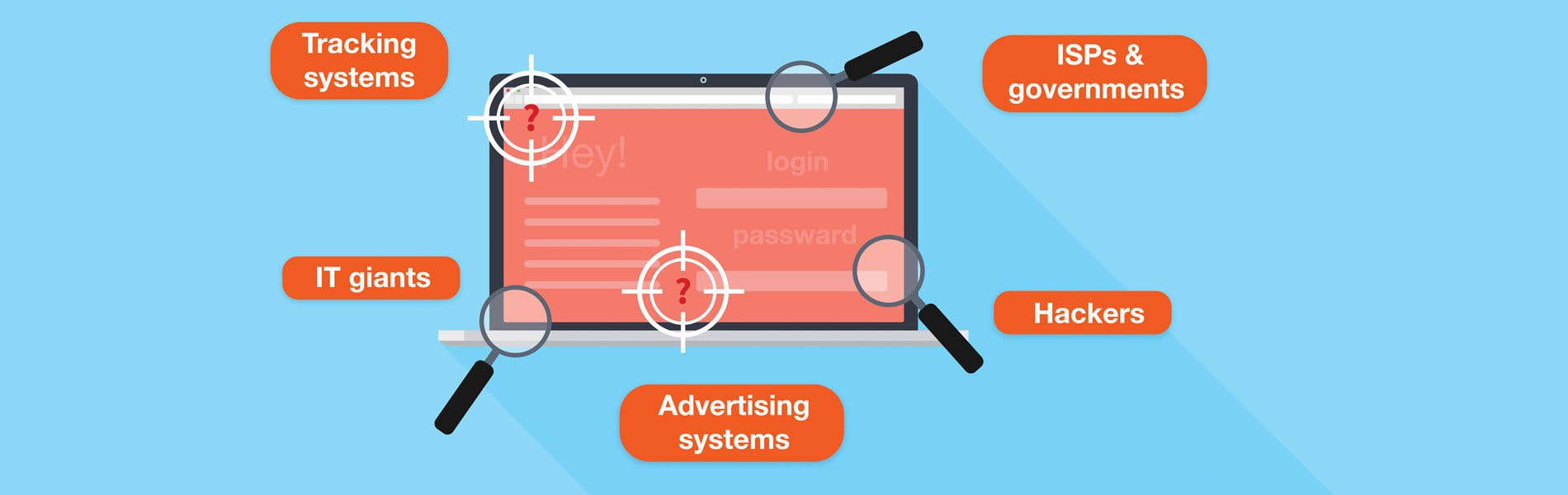
1. ISP’s & governments
A famous journalist and researcher James Bamford published an interesting article about a huge computing center in the USA, whose work is aimed at collecting and ordering all sources of information. According to his words, this center has all the necessary technologies to eavesdrop and record every telephone conversation, access any mailbox, intercept the transaction data and get to closed databases. For this, the agency cooperates with the leading ISP’s.
However, the US is not an exception. The UK authorities approved a law for the collection of personal data and access to sites that are used by the British. The law came into force in November 2015. According to the officials, this is the “limited set of specified purposes” subject to “strict controls.” In France and Germany, a similar scheme of supervising the online activities of citizens was launched the same year.
Also, many countries regulate what websites their citizens can visit. The latest example is Ukraine. Earlier in May, the authorities of the country banned access to some social networks, such as Vkontakte, Odnoklassniki, search engine Yandex, and email service Mail.ru. They claim that these measures have been taken for the sake of “protection measures”. But, as you know, hell is paved with good intentions.
2. IT giants
In our society, computerized systems of recording and storing information prevail. Every day billions of electronic letters pass through mail servers. Social networks stores more than a hundred megabytes of photos and videos about each user. Payment systems process a large amount of personally marked financial payments.
All these services we use daily can oversee not only pages we visit, but also the speed of our modem, the type of browser we use, and even our geographic location. You may ask: “If it’s really possible?” Well, yes, it is. There are some programs, like the US National Security Agency’s PRISM, which give the opportunity for IT giants get direct access to personal data stored in such resources like Google and Facebook. Moreover, Google Maps will track your location even without a geotag, just taking into account your calls, messages, and media files, which seems absolutely insignificant.
3. Advertising systems
Probably, there is no a single person who wouldn’t be annoyed by ads that are constantly reminding about themselves, popping-up in the middle of a movie, or while you are reading an article. Welcome to a secret world of marketing.
Usually advertising programs quietly run in the background. That is why it is difficult to detect them. They use this fact to their advantage, collecting and processing your personal data, such as IP address, browsers and email services you use, traffic information, duration of online sessions, web sites you visit. Having this info helps them to create your profile with specific interests and habits and show you more targeted ads.
How can marketers accurately determine the range of your interests? It’s very simple. Almost all web sites you visit contain third-party tracking scripts. If two sites use the same ad network, the data they store locally or as a cookie is shared between them. In fact, this allows them to bypass the restrictions.
Moreover, ads can be not only annoying. They can pose a serious threat to your online security. Some of them may contain malware that can harm your computer, by changing its settings or deleting important documents and files.
4. Tracking systems
At first glance, it’s a good idea to check-in in your favorite bar or cafe and post this on Facebook, Foursquare, Yelp, etc. This is a good chance to tell your friends about the places you like. There is also a flip side. To share this data, you need to specify your exact location, while this step may pose a huge threat to your online privacy.
One more case here is when you register in a place or publish a photo with geotags, the GPS coordinates with the exact address are usually added. If you do this at home, you disclose your residential address. This condition is perfect for offline criminals, letting them to penetrate into your real life.
That is, if you register in a restaurant, then you definitely are not at home. And this is known not only by your friends, but also by all concerned parties. The risks that come with advertising your behavior in social networks are large enough, so you should treat this with the utmost caution.
5. Hackers
Of course, scammers existed always and caused considerable damage at all times. With every new tool aimed at ensuring the security of users on the network, they come up with new ways to bypass them and get your data come what may.
Today, hackers write harmful code to get your personal data by installing an antivirus program, for instance. And how many times have you received a newsletter that you won a lottery? If you follow the link in such letter, you may become a victim of a phishing attack.
What about WiFi? It gives a great benefit for travelers and freelancers. But, technology geeks can get access to nearly all the gadgets that connect to a particular hotspot and monitor your every move on the screen.
Summarizing the results
According to the attorney Jennifer Lynch: “It’s pretty easy for the government to get access to the location data, and very hard for users to prevent that data from being gathered.” But it is your human right to use smartphones, computers, and tablets without worrying about being tracked.
Here are some tips that will help you to avoid the leakage of personal data:
- Turn off geo-location on your smartphone
- Delete your browser’s cookies regularly
- Encrypt the traffic your device sends and receives
- Manually select the Wi-Fi network you’re connecting to
- Regularly check and update security settings
Find more useful advices here.
Of course, nothing gives you 100% of online protection and security when you are connected to the internet. But it is really possible to reduce the level of risk. VPN Unlimited offers you a brand new feature, KeepSolid DNS Firewall. It allows you to:
- Block malicious websites, apps, which can harm your device
- Enable you to securely and anonymously surf the web and use apps without annoying ads
- Prevent any kind of intrusion into your private life, while you are online
- Keep out modern threats, such as man-in-the-middle attacks
- Block domains of the web tracking systems and advertising networks
Learn more about the benefits of our KeepSolid DNS Firewall here.
Download VPN Unlimited right away, and be one step ahead of scammers, not leaving them the opportunity to seize your data.