Which Statement Describes a VPN

Wondering what is a Virtual Private Network solution and whether you need it? You’ve landed in the right place! In this piece, we are going to answer a few questions about Virtual Private Networks, consider their working principle, and figure out which statement describes a VPN most comprehensively.
First of all, let’s start with the VPN definition. A Virtual Private Network, abbreviated as VPN, is a secure connection created through a public network and acts as a facilitator between your device and the internet. These solutions allow you to stay anonymous online, virtually travel worldwide, gain unrestricted access to any content, and be sure your sensitive data is reliably ciphered.
Thanks to VPN Unlimited - our credible VPN app, you can browse the web like a pro user on the following devices:
- iOS & Android phones and tablets
- macOS, Windows, and Linux laptops
- Routers and game consoles
- Smart TVs and streaming devices
- Chrome, Mozilla, and Opera browsers
Let’s Dive into the Virtual Private Networks History

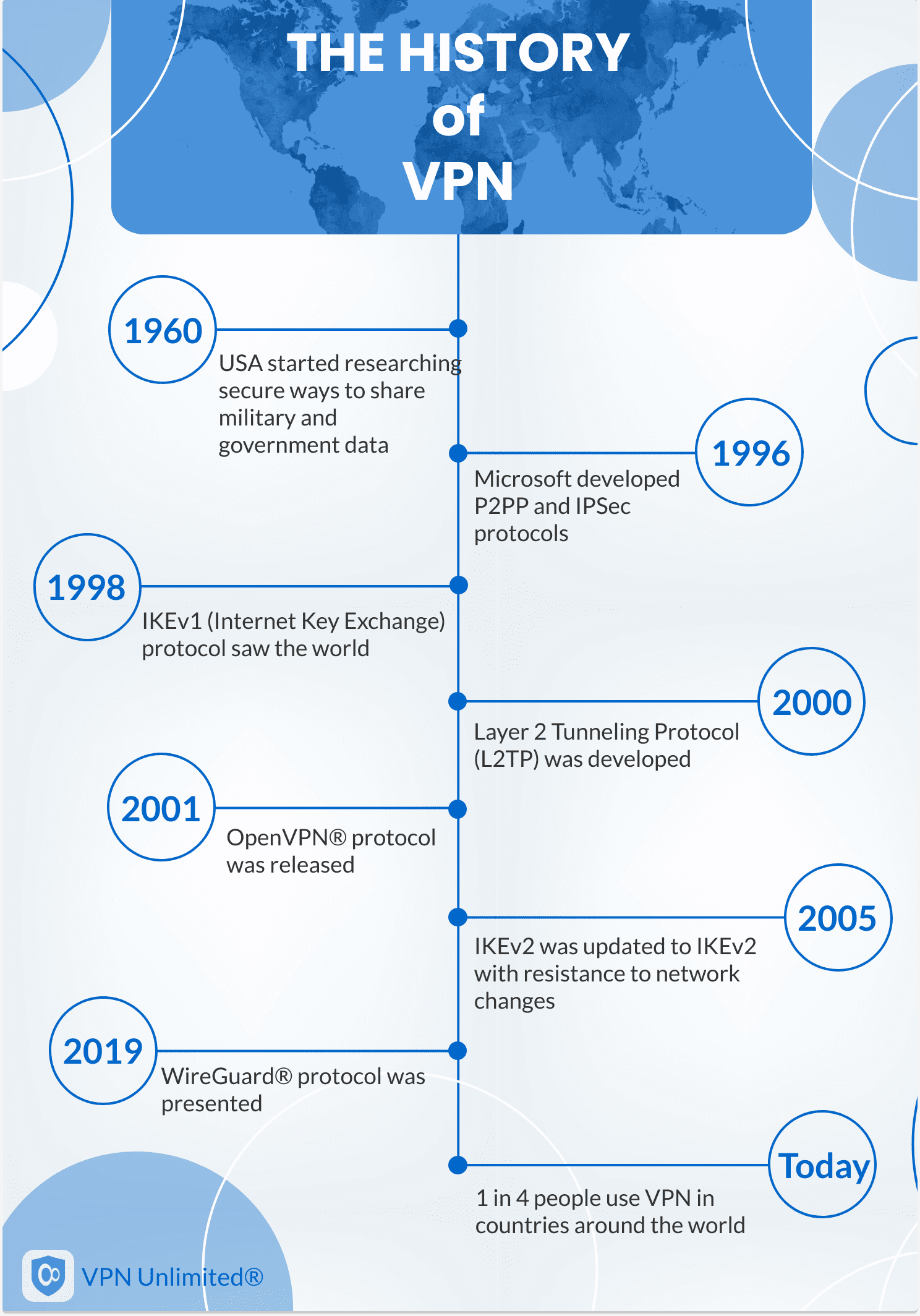
The history of Virtual Private Networks starts back in the 1960s when the internet was launched. U.S. Department of Defense started researching secure ways to share military and government information and implementing electronic methods of remote communication.
Another important date in VPN history is 1996 year when Microsoft developed PPTP (Peer-to-Peer Tunneling) and IPSec (Internet Protocol Security) protocols.
Let’s move on. In 1998, IKEv1, or Internet Key Exchange protocol, was developed. This protocol was used for secure encryption keys exchanging and establishing private communication between two devices.
The 2000 year brought the Layer 2 Tunneling Protocol, also known as L2TP. According to the statement, this protocol supported, and still supports, virtual private connections and helps ISPs deliver their services. However, L2TP provided zero encryption. So, L2TP was always (and continues to be) used with IPSec.
A turning point in VPN history was in 2001 when the OpenVPN® protocol was developed. It was the first open-source virtual protocol that offered great security achieved by mixing TLS and SSL protocols.
In 2005, IKEv1 was officially updated to IKEv2 with fixed security vulnerabilities and resistance to network changes. From now on, the VPN connection wouldn't go down if you switched from a WiFi network to cellular data and vice versa.
10 years of Virtual Private Network popularization among private users, and in 2019, the WireGuard® protocol was presented.
For now, Virtual Private Networks keep growing and becoming even more secure. Today 1 in 4 people use a VPN in countries around the world. So do you! Get VPN Unlimited on your device and ensure your internet traffic is protected from the prying eyes!
Benefits of Using the VPN Unlimited App
- Protection against hackers: Our Virtual Private Network reliably encrypts traffic of your device
- Online anonymity: VPN Unlimited hides your actual IP address and geographical location
- Safe browsing on public WiFi: VPN ciphers all of your data while you use an unsecured network
- Unrestricted access: Our security app allows bypassing any restrictions and accessing previously blocked sites
- Regional pricing: VPN Unlimited makes your online shopping more beneficial and secure
Steps to Get Started with VPN Unlimited
Choose your perfect subscription
and get extra 7 days for free
Create your KeepSolid ID and
connect to the desired location
Ready to Start Your Safe and Unrestricted Online Journey?
Get VPN Unlimited right now and say Yes to unblocking any internet content, secure web browsing, and bulletproof traffic encryption!
Which Statement Describes a VPN Working Principle
According to the VPN statement, it is sophisticated software that aims to protect your privacy, anonymity, and sensitive data online.
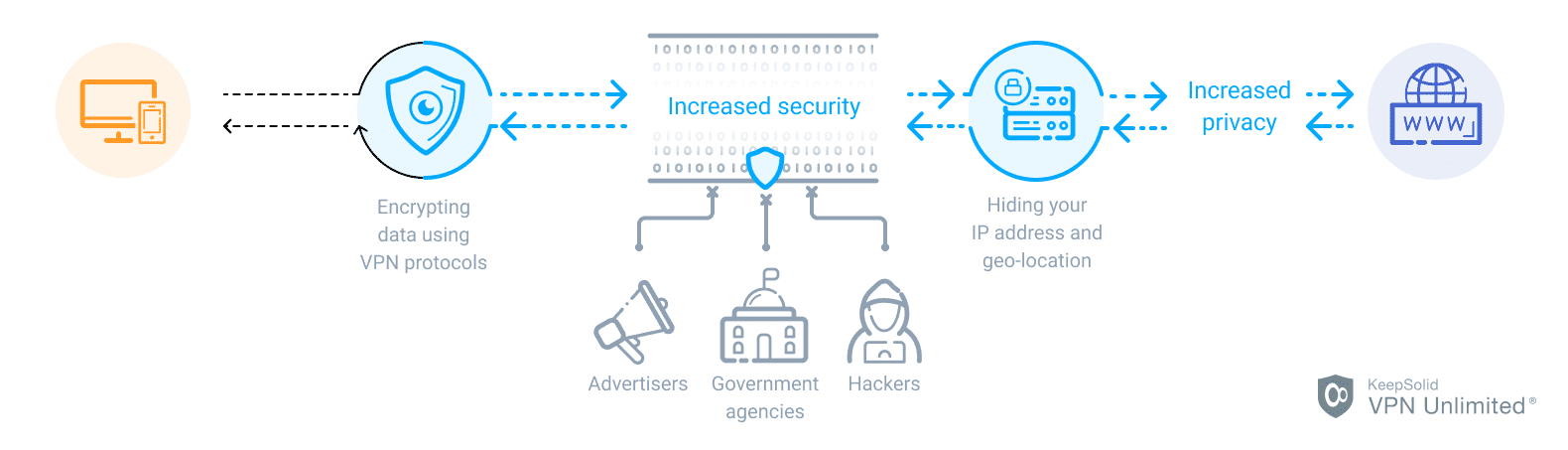
To provide you with the highest security possible, VPN Unlimited encrypts all your data with military-grade AES 256-bit encryption. This algorithm encodes both the incoming and outgoing internet traffic in such a way that only authorized parties can decipher and read it. If any unauthorized user tries to decrypt this data, the only thing they can get is a bunch of incomprehensible symbols.
After your traffic is reliably encrypted, our security solution transmits it through the impenetrable tunnel that is established between your device and chosen virtual server. As a result, neither your ISP nor cyber criminals can detect your actual IP address and geo-location. Thus, you become anonymous and untrackable online.
More Statements about Virtual Private Network Solutions
Download VPN Unlimited Right Now
AES-256 encryption, bulletproof virtual protocols, Kill Switch feature, and many other options to make your online life secure and unrestricted are waiting for you. Do not come to think which statement describes a VPN most comprehensively - check it for yourself!
